The Transform Technology Summits begin October 13th with Low-Code/No Code: Enabling Enterprise Agility. Register now!
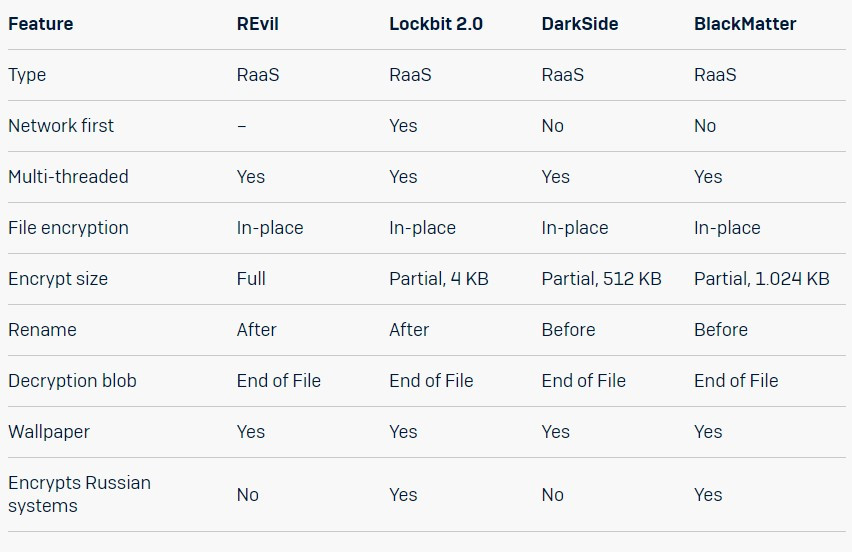
New study from SophosLabs shows that there is a connection amongst BlackMatter and DarkSide ransomware. However, this is not a basic case of rebranding. Sophos’ evaluation of the malware shows that though there are similarities with DarkSide ransomware, the code is not identical.
In late July, a new RaaS appeared on the scene. Calling itself BlackMatter, the ransomware claims to fill the void left by DarkSide and REvil — adopting the most effective tools and tactics from every of them, as effectively as from the nonetheless-active LockBit 2.. They also say that though they are closely acquainted with the Darkside operators, they are not the similar individuals.
As the alleged operators behind the ransomware have claimed, there are also similarities with REvil and LockBit 2. ransomware. For instance, in a shared similarity with each REvil and Darkside, BlackMatter ransomware retailers configuration information and facts in the binary in an encoded format.
SophosLabs decoded this and located that BlackMatter ransomware has a related structure and information and facts stored in the configuration blob, like lists of processes and services to kill, the ransom note, C2 specifics, directories to keep away from and so forth. Additionally, like DarkSide (and REvil), BlackMatter utilizes a run-time API that can hinder static evaluation of the malware.
Like the other two ransomware groups, strings are also encrypted and revealed for the duration of runtime. Sophos also located a couple of features that are distinct to BlackMatter. One of these is its capacity to reset file permissions so that everybody can view a document – simply because of the malicious encryption that follows, this does not instantly bring about a breach of privacy.
However, victims who spend the ransom demand will acquire a decrypter from the attacker that can not restore the original access permissions as this safety information and facts has been lost. IT admins must verify and re-enforce correct permissions when recovering from a BlackMatter ransomware attack.
It’s nonetheless early days for this new ransomware-as-a-service family, but this study suggests that in the hands of an skilled attacker, this ransomware can bring about a lot of harm with no triggering lots of alarms. It is essential for defenders to promptly investigate endpoint protection alerts as they can be an indication of an imminent attack with potentially disastrous consequences.
These findings are based on a deep dive evaluation of the BlackMatter malware by SophosLabs as effectively as a Sophos Rapid Response investigation into an incident involving BlackMatter ransomware.
Read the complete report by SophosLabs





/cdn.vox-cdn.com/uploads/chorus_asset/file/25547838/YAKZA_3840_2160_A_Elogo.jpg)
